Working with Library Profiles
How to use library profiles to apply configuration
Overview
This section of our configuration guide assumes knowledge of library profiles and scope IDs. If you are not yet familiar with topics please first review our library profile and scope ID guides. In Central, configuration profiles are assigned to scopes within the hierarchy to apply the configuration. For example, assigning a VLAN profile to a site scope will apply said VLAN configuration to every applicable device function in the site.
Assigning Library Profiles
Profiles can be applied to scopes in the Central UI or through API. For both methods you will need to designate a device function and a scope for your profile. The device function will designate which type of devices the profile will be applied to. The scope will designate which level of the hierarchy the profile will be applied to.
Assigning with Central UI
-
Navigate to a profile management card in the library and find the three menu dots at the end of the row
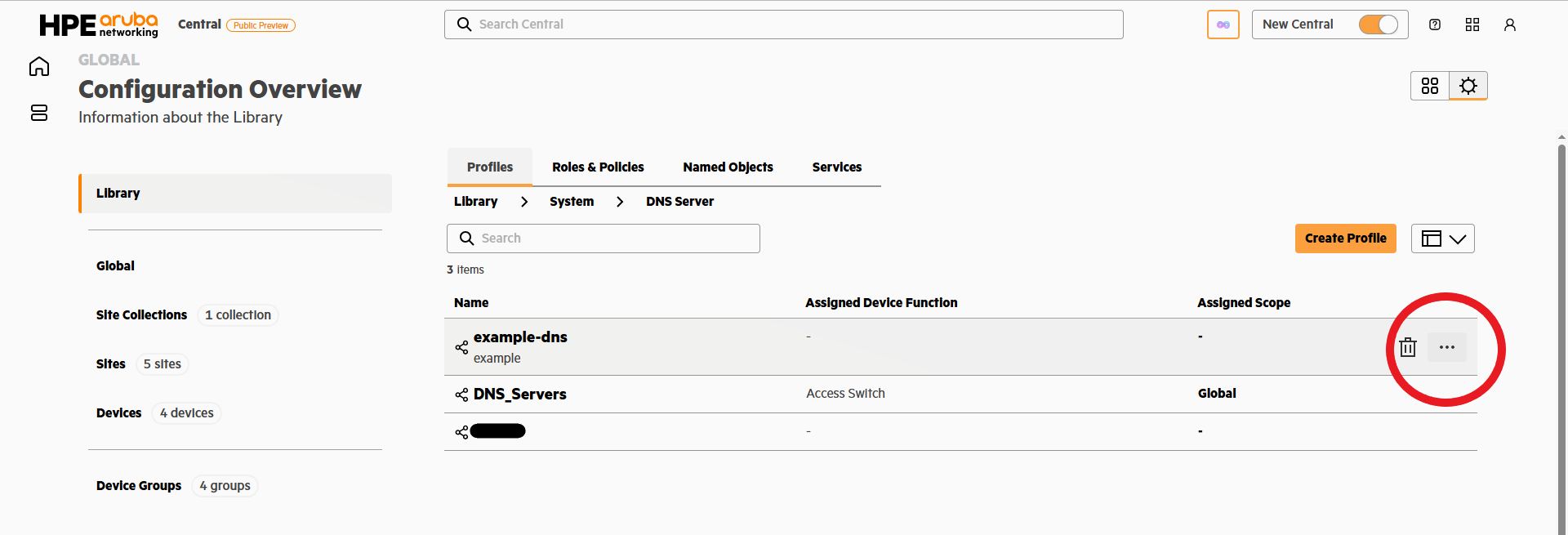
-
Expand the menu and select assign
-
Select a device function
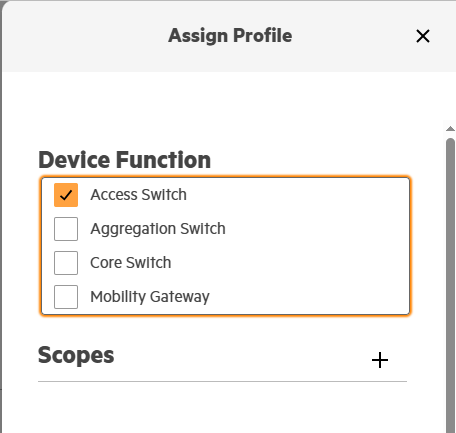
-
Select a scope level and scope
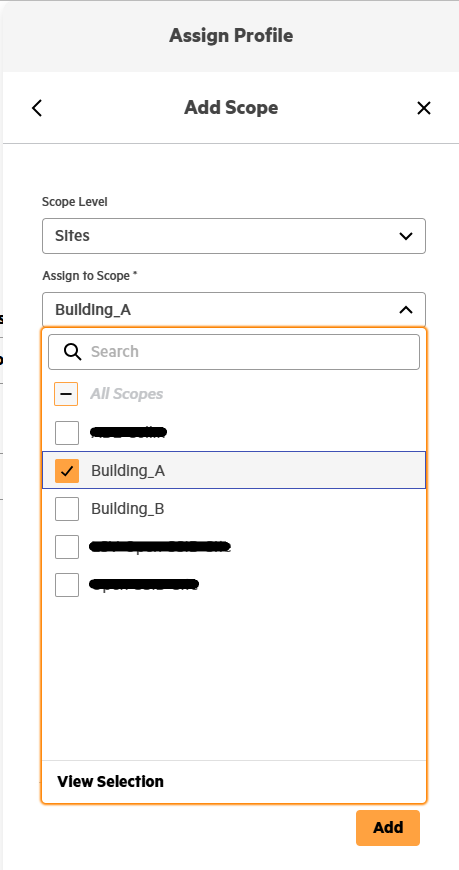
-
Finish by pressing the 'Add' button
Profiles are flexible
A profile can be assigned to multiple device functions and scopes using the same workflow.
Assigning with Central API
To assign profiles to scopes using the REST API we will use the scope-maps endpoint. This requires gathering preliminary information to provide in the API payload, including the scope ID, persona, and resource. For more information about working with Central API please visit our Getting Started with REST APIs guide. You can get started quickly with APIs using our Postman Collection guide.
- Get the scope ID for the scope that we want to assign a profile to. Please reference our Scope ID guide for full details on this process.
- Lookup the API persona that is equivalent to the device function from the Central UI. Please reference our Device Function and Persona guide for a full table of personas and their device function equivalent.
- Define the resource. The resource is a string combination of the API endpoint of the profile type and the name/identifier of the profile. For example to assign a VLAN profile with the ID 404 the resource string would be "layer2-vlan/404". Please reference the Configuration API Reference for individual endpoints.
Postman Example
With the above information gathered we can use the scope-maps API to populate the payload. Here is an example using postman with all the information we've collected.
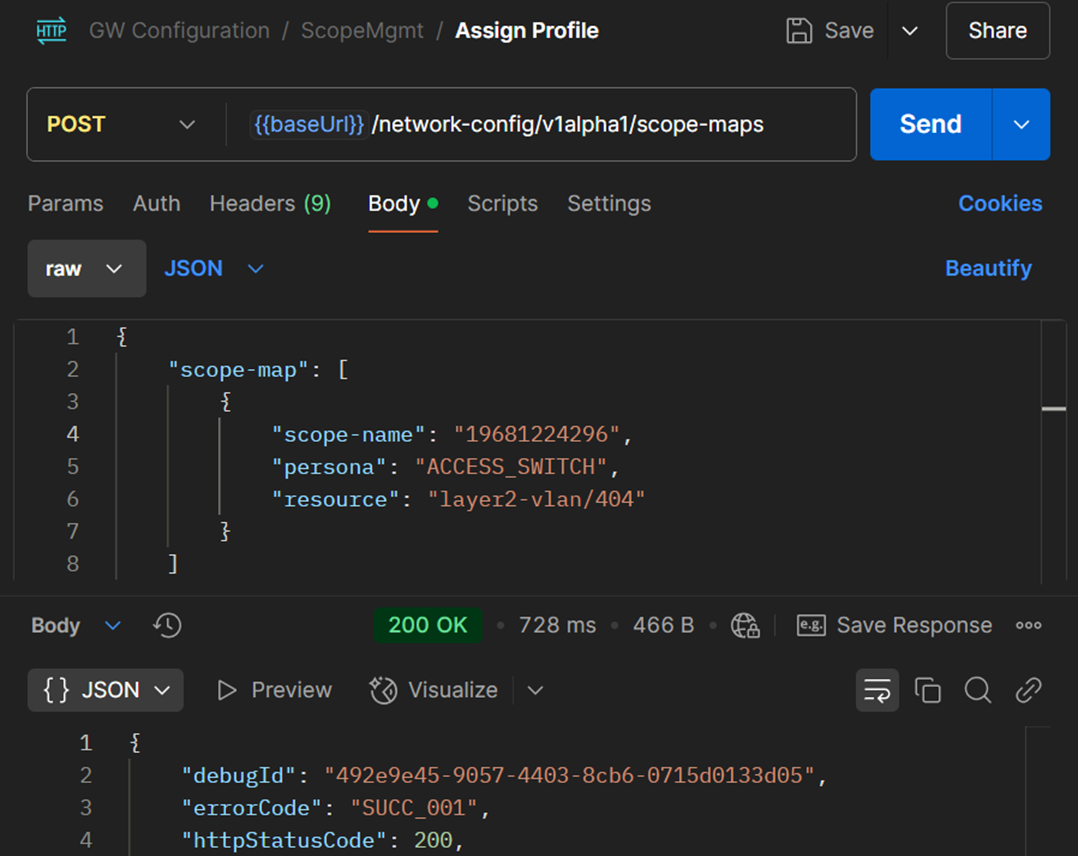
Postman VLAN example
Curl Example
curl --request POST \
--url https://{base_url}/network-config/v1alpha1/scope-maps \
--header 'accept: application/json' \
--header 'authorization: Bearer {{token}}' \
--header 'content-type: application/json' \
--data '
{
"scope-map": [
{
"scope-name": "1234567",
"persona": "ACCESS_SWITCH",
"resource": "layer2-vlan/404"
}
]
}
'
Upon receiving a successful response our Library Profile is now properly assigned to our scope!
Unassigning Library Profiles
Unassign with Central UI
-
Navigate to a profile management card in the library and find the three menu dots at the end of the row

-
Click the option to unassign which will make a popup windows appear. Next check the box of the scope name that you would like to unassign. Finally, confirm with the unassign button.
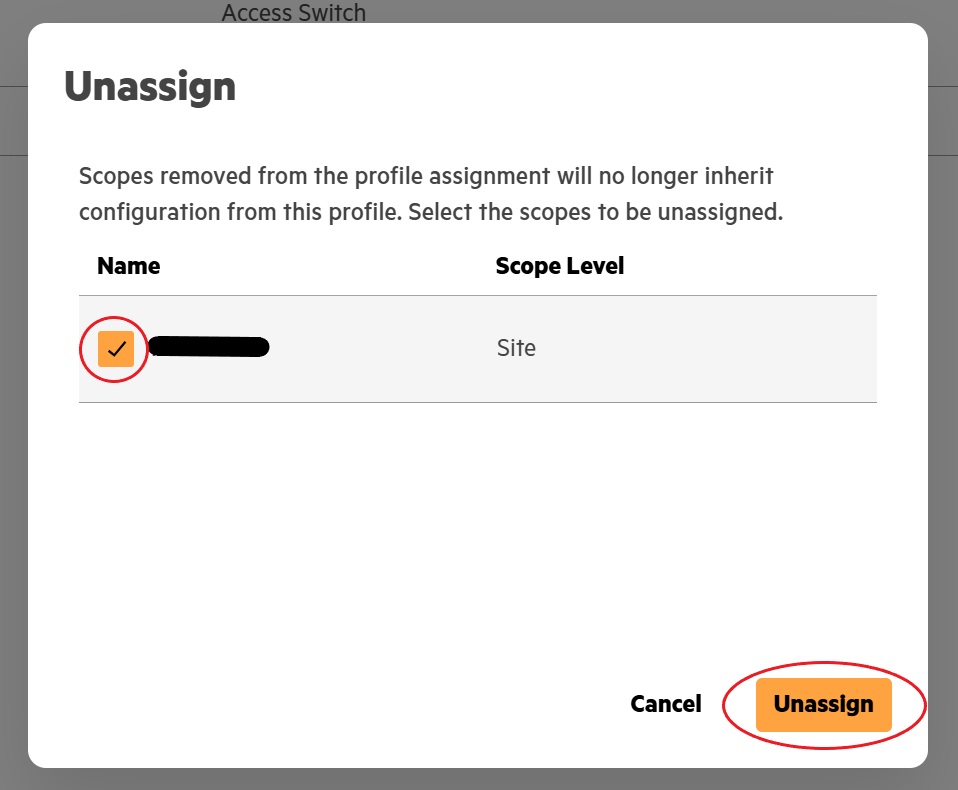
Unassign with Central API
Unassigning a profile with Central API is slightly different than creating. Follow the same instructions for assigning with API to gather the required information. Except, instead of using the gathered information for a body object, we will use them in the path.
Postman Example
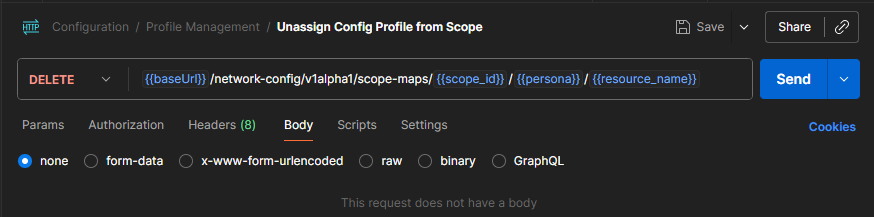
Curl Example
curl --request DELETE \
--url https://internal.api.central.arubanetworks.com/network-config/v1alpha1/scope-maps/{{scope_id}}/{{persona}}/{{resource_name}} \
--header 'accept: application/json' \
--header 'authorization: Bearer {{token}}'
Updated 4 months ago
Now that you've explored working with Library Profiles, check out working with Local Profiles